Table of Contents
Run your own SIP VoIP service on both IPv4 and IPv6
Main author:
Daniel-Constantin Mierla <miconda [at] gmail.com>
- founder Kamailio SIP Server project
At the date of publishing the article, the world celebrated IPv6 day, a good opportunity to show how to build your own SIP-based VoIP service to run on both IPv4 and IPv6 networks using open source Kamailio SIP server.
Kamailio has support for IPv6 since 2002, but since the presence of IPv6 networks was not a part of reality, its usage was quite limited in the past. Also we tested the core and the most used modules last year at the SIPit event in Sweden. Now the interest has increased substantially, a fact visible also in the subject of the topics discussed on project's forums.
The target with this tutorial is to have a service that is able to handle VoIP traffic:
- in IPv4 networks
- in IPv6 networks
- bridge between IPv4 and IPv6 networks when needed
Kamailio itself is a SIP signaling server, therefore it will take care of bridging the SIP traffic. To bridge the media stream between IPv4 and IPv6, we will use RTPProxy, an application used so far mainly to help with NAT traversal in IPv4 networks.
Did I say NAT? Fortunately it will disappear soon, when (if) IPv6 will take the control in Internet communications.
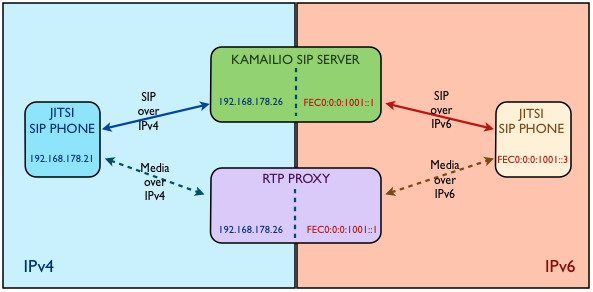
About the environment
To make the guidelines for this tutorial, I built a local lab environment where I used:
- Kamailio devel version running on Ubuntu 11.04 with next IP addresses:
- IPv4: 192.168.178.26
- IPv6: fec0:0:0:1001::1
- Jitsi SIP softphone running on Mac OS X with next IP address:
- IPv4: 192.168.178.21
- Jitsi SIP softphone running on Ubuntu 10.10 with next IP address:
- IPv6: fec0:0:0:1001::3
To install Kamailio devel version (to become 3.2.0 release in Autumn 2011), use following guidelines:
However, the same concept can be applied to the latest stable v3.1.x, just use the appropriate functions from rtpproxy module - the development version introduced a new function rtpproxy_manage() which is a wrapper around existing functions in v3.1.x: rtpproxy_offer(), rtpproxy_answer() and unforce_rtp_proxy() – the parameters have the same meanings both versions.
Debian/Ubuntu users can install Kamailio development version from the APT repository (nightly builds), see:
- Debian/Ubuntu APT repository for Kamailio devel version (you will need to adapt mpath parameter in kamailio.cfg - see notes later in this document)
Jitsi is a cross platform (Linux, Mac OS X and Windows) open source SIP softphone available at:
FYI: I tested also with Linphone on IPv6 and seemed to be fine – a side not: Linphone for Mac OS X didn't have support for video and I wanted to test also multi-streams IPv4-IPv6 bridging (audio and video in this case).
RTPProxy is available at:
- for this article I installed RTPProxy from Ubuntu default APT repository with:
apt-get install rtpproxy
RTPProxy creates a special user (named rtpproxy) to run under unprivileged permissions. You have to allow Kamailio to communicate with it via control socket. One easy way is to edit /etc/init.d/rtpproxy and set the running user ID to kamailio since it is the only application accessing it, like:
USER=kamailio
Note that RTPProxy has to be started with special parameters in order o bridge between IPv4 and IPv6 addresses:
-l ADDR_IPV4 -6 /ADDR_IPV6
You have to change the /etc/init.d/rtpproxy to add these parameters.
Sample Scenario
I called using one Jitsi phone on IPv6 and one on IPv4, turning on video conversation – this is the most interesting case in my opinion: bridging real-time communication between IPv6 and IPv4 networks.
Here is the result - I is talking to me.
SIP Traffic
For the technical guys, I pasted below the relevant SIP signaling messages for this call (I stripped some of the SDP content since it was too big and irrelevant for this case – just codecs attributes).
Some remarks about the SIP traffic:
- call comes in from IPv6 (frame [1] INVITE) with headers and SDP body filled with IPv6 addresses
- when the call is forwarded by Kamailio to callee (frame [2]), you can observe:
- presence of two Record-Route heders, one with Kamailio's IPv4 address and the other with Kamailio's IPv6 address
- although incoming INVITE had SDP body with caller's IPv6 address, now the SDP body has RTPProxy IPv4 address since the INVITE is sent to IPv4 network
- when call is answered, the 200ok SIP replies comes in from callee (frame [3]), with IPv4 addresses in SDP body
- then the 200ok reply is relayed to caller (frame [4]), but now the SDP body has the IPv6 address of RTPProxy
- the communication is ready to start, each side sending packets only in one type of network. SIP routing is driven by Record-Route headers and RTP by IP address in SDP body.
[1] fec0:0:0:1001::3.5060 > fec0:0:0:1001::1.5060 INVITE sip:102@[fec0:0:0:1001::1] SIP/2.0 Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 CSeq: 2 INVITE From: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 To: <sip:102@[fec0:0:0:1001::1]> Via: SIP/2.0/UDP [fec0:0:0:1001:0:0:0:3]:5060;branch=z9hG4bK-373838-0724cc1aa770fb3d7a70a456274bd649 Max-Forwards: 70 Contact: "103" <sip:103@[fec0:0:0:1001:0:0:0:3]:5060;transport=udp;registering_acc=[fec0:0:0:1001::1]> User-Agent: Jitsi1.0-beta1-nightly.build.3522Linux Content-Type: application/sdp Content-Length: 875 v=0 o=103 0 0 IN IP6 fec0:0:0:1001:0:0:0:3 s=- c=IN IP6 fec0:0:0:1001:0:0:0:3 t=0 0 m=audio 5004 RTP/AVP 9 96 97 0 8 98 3 99 5 6 4 15 101 a=rtpmap:9 G722/8000 ... [2] 192.168.178.26.5060 > 192.168.178.21.5060 INVITE sip:102@192.168.178.21:5060;transport=udp;registering_acc=192_168_178_26 SIP/2.0 Record-Route: <sip:192.168.178.26;r2=on;lr=on;nat=v46> Record-Route: <sip:[FEC0:0:0:1001:0:0:0:1];r2=on;lr=on;nat=v46> Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 CSeq: 2 INVITE From: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 To: <sip:102@[fec0:0:0:1001::1]> Max-Forwards: 69 Contact: "103" <sip:103@[fec0:0:0:1001:0:0:0:3]:5060;transport=udp;registering_acc=[fec0:0:0:1001::1]> User-Agent: Jitsi1.0-beta1-nightly.build.3522Linux Content-Type: application/sdp Via: SIP/2.0/UDP 192.168.178.26;branch=z9hG4bK0099.a33fcf56.0 Via: SIP/2.0/UDP [fec0:0:0:1001:0:0:0:3]:5060;rport=5060;branch=z9hG4bK-373838-da2adaf5a3c34a1de259916f79ba11b7 Content-Length: 881 v=0 o=103 0 0 IN IP4 192.168.178.26 s=- c=IN IP4 192.168.178.26 t=0 0 m=audio 61536 RTP/AVP 9 96 97 0 8 98 3 99 5 6 4 15 101 a=rtpmap:9 G722/8000 ... a=nortpproxy:yes [3] 192.168.178.21.5060 > 192.168.178.26.5060 SIP/2.0 200 OK To: <sip:102@[fec0:0:0:1001::1]>;tag=7e28fdba Via: SIP/2.0/UDP 192.168.178.26;branch=z9hG4bK0099.a33fcf56.0,SIP/2.0/UDP [fec0:0:0:1001:0:0:0:3]:5060;rport=5060;branch=z9hG4bK-373838-da2adaf5a3c34a1de259916f79ba11b7 Record-Route: <sip:192.168.178.26;r2=on;lr=on;nat=v46>,<sip:[FEC0:0:0:1001:0:0:0:1];r2=on;lr=on;nat=v46> CSeq: 2 INVITE Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 From: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 Contact: "102" <sip:102@192.168.178.21:5060;transport=udp;registering_acc=192_168_178_26> User-Agent: Jitsi1.0-beta1-nightly.build.3521Mac OS X Content-Type: application/sdp Content-Length: 781 v=0 o=102 0 0 IN IP4 192.168.178.21 s=- c=IN IP4 192.168.178.21 t=0 0 m=audio 5008 RTP/AVP 9 96 97 0 8 98 99 5 6 15 101 a=rtpmap:9 G722/8000 ... [4] fec0:0:0:1001::1.5060 > fec0:0:0:1001::3.5060 SIP/2.0 200 OK To: <sip:102@[fec0:0:0:1001::1]>;tag=7e28fdba Via: SIP/2.0/UDP [fec0:0:0:1001:0:0:0:3]:5060;rport=5060;branch=z9hG4bK-373838-da2adaf5a3c34a1de259916f79ba11b7 Record-Route: <sip:192.168.178.26;r2=on;lr=on;nat=v46>,<sip:[FEC0:0:0:1001:0:0:0:1];r2=on;lr=on;nat=v46> CSeq: 2 INVITE Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 From: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 Contact: "102" <sip:102@192.168.178.21:5060;transport=udp;registering_acc=192_168_178_26> User-Agent: Jitsi1.0-beta1-nightly.build.3521Mac OS X Content-Type: application/sdp Content-Length: 805 v=0 o=102 0 0 IN IP6 fec0:0:0:1001::1 s=- c=IN IP6 fec0:0:0:1001::1 t=0 0 m=audio 38516 RTP/AVP 9 96 97 0 8 98 99 5 6 15 101 a=rtpmap:9 G722/8000 ... a=nortpproxy:yes [5] fec0:0:0:1001::3.5060 > fec0:0:0:1001::1.5060 ACK sip:102@192.168.178.21:5060;transport=udp;registering_acc=192_168_178_26 SIP/2.0 Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 CSeq: 2 ACK Via: SIP/2.0/UDP [fec0:0:0:1001:0:0:0:3]:5060;branch=z9hG4bK-373838-cb66ec5365d63fe8e6f3f81ab0f66a7b From: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 To: "102" <sip:102@[fec0:0:0:1001::1]>;tag=7e28fdba Max-Forwards: 70 Route: <sip:[FEC0:0:0:1001:0:0:0:1];r2=on;lr=on;nat=v46>,<sip:192.168.178.26;r2=on;lr=on;nat=v46> Contact: "103" <sip:103@[fec0:0:0:1001:0:0:0:3]:5060;transport=udp;registering_acc=[fec0:0:0:1001::1]> User-Agent: Jitsi1.0-beta1-nightly.build.3522Linux Content-Length: 0 [6] 192.168.178.26.5060 > 192.168.178.21.5060 ACK sip:102@192.168.178.21:5060;transport=udp;registering_acc=192_168_178_26 SIP/2.0 Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 CSeq: 2 ACK Via: SIP/2.0/UDP 192.168.178.26;branch=z9hG4bKcydzigwkX Via: SIP/2.0/UDP [fec0:0:0:1001:0:0:0:3]:5060;rport=5060;branch=z9hG4bK-373838-cb66ec5365d63fe8e6f3f81ab0f66a7b From: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 To: "102" <sip:102@[fec0:0:0:1001::1]>;tag=7e28fdba Max-Forwards: 69 Contact: "103" <sip:103@[fec0:0:0:1001:0:0:0:3]:5060;transport=udp;registering_acc=[fec0:0:0:1001::1]> User-Agent: Jitsi1.0-beta1-nightly.build.3522Linux Content-Length: 0 [7] 192.168.178.21.5060 > 192.168.178.26.5060 BYE sip:103@[fec0:0:0:1001:0:0:0:3]:5060;transport=udp;registering_acc=[fec0:0:0:1001::1] SIP/2.0 CSeq: 1 BYE From: <sip:102@[fec0:0:0:1001::1]>;tag=7e28fdba To: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 Max-Forwards: 70 Route: <sip:192.168.178.26;r2=on;lr=on;nat=v46>,<sip:[FEC0:0:0:1001:0:0:0:1];r2=on;lr=on;nat=v46> Via: SIP/2.0/UDP 192.168.178.21:5060;branch=z9hG4bK-393630-97675b8dfcf6c8698398b150cdb24845 Contact: "102" <sip:102@192.168.178.21:5060;transport=udp;registering_acc=192_168_178_26> User-Agent: Jitsi1.0-beta1-nightly.build.3521Mac OS X Content-Length: 0 [8] fec0:0:0:1001::1.5060 > fec0:0:0:1001::3.5060 BYE sip:103@[fec0:0:0:1001:0:0:0:3]:5060;transport=udp;registering_acc=[fec0:0:0:1001::1] SIP/2.0 CSeq: 1 BYE From: <sip:102@[fec0:0:0:1001::1]>;tag=7e28fdba To: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 Max-Forwards: 69 Via: SIP/2.0/UDP [FEC0:0:0:1001:0:0:0:1];branch=z9hG4bK3099.f30b84.0 Via: SIP/2.0/UDP 192.168.178.21:5060;rport=5060;branch=z9hG4bK-393630-97675b8dfcf6c8698398b150cdb24845 Contact: "102" <sip:102@192.168.178.21:5060;transport=udp;registering_acc=192_168_178_26> User-Agent: Jitsi1.0-beta1-nightly.build.3521Mac OS X Content-Length: 0 [9] fec0:0:0:1001::3.5060 > fec0:0:0:1001::1.5060 SIP/2.0 200 OK To: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 Via: SIP/2.0/UDP [FEC0:0:0:1001:0:0:0:1];branch=z9hG4bK3099.f30b84.0;received=fec0:0:0:1001:0:0:0:1,SIP/2.0/UDP 192.168.178.21:5060;rport=5060;branch=z9hG4bK-393630-97675b8dfcf6c8698398b150cdb24845 CSeq: 1 BYE Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 From: <sip:102@[fec0:0:0:1001::1]>;tag=7e28fdba Contact: "103" <sip:103@[fec0:0:0:1001:0:0:0:3]:5060;transport=udp;registering_acc=[fec0:0:0:1001::1]> User-Agent: Jitsi1.0-beta1-nightly.build.3522Linux Content-Length: 0 [10] 192.168.178.26.5060 > 192.168.178.21.5060 SIP/2.0 200 OK To: "103" <sip:103@[fec0:0:0:1001::1]>;tag=3891da55 Via: SIP/2.0/UDP 192.168.178.21:5060;rport=5060;branch=z9hG4bK-393630-97675b8dfcf6c8698398b150cdb24845 CSeq: 1 BYE Call-ID: cc8f5a3f528f880e3caabbf11605b0c2@0:0:0:0:0:0:0:0 From: <sip:102@[fec0:0:0:1001::1]>;tag=7e28fdba Contact: "103" <sip:103@[fec0:0:0:1001:0:0:0:3]:5060;transport=udp;registering_acc=[fec0:0:0:1001::1]> User-Agent: Jitsi1.0-beta1-nightly.build.3522Linux Content-Length: 0
Location Records
The location records in Kamailio taken with kamctl looked like:
# kamctl ul show Domain:: location table=512 records=2 max_slot=1 AOR:: 102 Contact:: sip:102@192.168.178.21:5060;transport=udp;registering_acc=192_168_178_26 Q= Expires:: 562 Callid:: 54cf25d15fe668a1d542616093f99c70@0:0:0:0:0:0:0:0 Cseq:: 2 User-agent:: Jitsi1.0-beta1-nightly.build.3521Mac OS X Received:: sip:192.168.178.21:5060 State:: CS_DIRTY Flags:: 0 Cflag:: 2 Socket:: udp:192.168.178.26:5060 Methods:: 4294967295 AOR:: 103 Contact:: sip:103@[fec0:0:0:1001:0:0:0:3]:5060;transport=udp;registering_acc=[fec0:0:0:1001::1] Q= Expires:: 596 Callid:: b5291cb60c79d65c65291364c7103138@0:0:0:0:0:0:0:0 Cseq:: 2 User-agent:: Jitsi1.0-beta1-nightly.build.3522Linux State:: CS_DIRTY Flags:: 0 Cflag:: 64 Socket:: udp:[FEC0:0:0:1001:0:0:0:1]:5060 Methods:: 4294967295
Kamailio Configuration File
The configuration file for IPv4-IPv6 support is available for download further down. You have to copy it over /usr/local/etc/kamailio/kamailio.cfg.
Then you have to edit it and update the values for IPv4 and IPv6 addresses acording to your environment, search the lines:
#!define ADDR_IPV4 192.168.178.26 #!define ADDR_IPV6 [fec0:0:0:1001::1]
Then you are ready to go - start kamailio with this configuration file.
To check if it is listening on both IPv4 and IPv6, use kamctl tool:
# kamctl ps Process:: ID=0 PID=4047 Type=attendant Process:: ID=1 PID=4048 Type=udp receiver child=0 sock=192.168.178.26:5060 Process:: ID=2 PID=4049 Type=udp receiver child=1 sock=192.168.178.26:5060 Process:: ID=3 PID=4050 Type=udp receiver child=2 sock=192.168.178.26:5060 Process:: ID=4 PID=4051 Type=udp receiver child=3 sock=192.168.178.26:5060 Process:: ID=5 PID=4052 Type=udp receiver child=0 sock=[FEC0:0:0:1001:0:0:0:1]:5060 Process:: ID=6 PID=4053 Type=udp receiver child=1 sock=[FEC0:0:0:1001:0:0:0:1]:5060 Process:: ID=7 PID=4054 Type=udp receiver child=2 sock=[FEC0:0:0:1001:0:0:0:1]:5060 Process:: ID=8 PID=4055 Type=udp receiver child=3 sock=[FEC0:0:0:1001:0:0:0:1]:5060 Process:: ID=9 PID=4056 Type=slow timer Process:: ID=10 PID=4057 Type=timer Process:: ID=11 PID=4059 Type=MI FIFO Process:: ID=12 PID=4063 Type=ctl handler Process:: ID=13 PID=4064 Type=TIMER NH Process:: ID=14 PID=4067 Type=tcp receiver child=0 Process:: ID=15 PID=4068 Type=tcp receiver child=1 Process:: ID=16 PID=4069 Type=tcp receiver child=2 Process:: ID=17 PID=4070 Type=tcp receiver child=3 Process:: ID=18 PID=4072 Type=tcp main process
You can spot easily the UDP receivers on IPv6 address.
kamailio.cfg
Here is the content you have to place in /usr/local/etc/kamailio/kamailio.cfg:
#!KAMAILIO # # Kamailio (OpenSER) SIP Server v3.2 - default configuration script # - web: http://www.kamailio.org # - git: http://sip-router.org # # Direct your questions about this file to: <sr-users@lists.sip-router.org> # # Refer to the Core CookBook at http://www.kamailio.org/dokuwiki/doku.php # for an explanation of possible statements, functions and parameters. # # Several features can be enabled using '#!define WITH_FEATURE' directives: # # *** To run in debug mode: # - define WITH_DEBUG # # *** To enable mysql: # - define WITH_MYSQL # # *** To enable authentication execute: # - enable mysql # - define WITH_AUTH # - add users using 'kamctl' # # *** To enable IP authentication execute: # - enable mysql # - enable authentication # - define WITH_IPAUTH # - add IP addresses with group id '1' to 'address' table # # *** To enable persistent user location execute: # - enable mysql # - define WITH_USRLOCDB # # *** To enable presence server execute: # - enable mysql # - define WITH_PRESENCE # # *** To enable nat traversal execute: # - define WITH_NAT # - install RTPProxy: http://www.rtpproxy.org # - start RTPProxy: # rtpproxy -l _your_public_ip_ -s udp:localhost:7722 # # *** To enable PSTN gateway routing execute: # - define WITH_PSTN # - set the value of pstn.gw_ip # - check route[PSTN] for regexp routing condition # # *** To enable database aliases lookup execute: # - enable mysql # - define WITH_ALIASDB # # *** To enable speed dial lookup execute: # - enable mysql # - define WITH_SPEEDDIAL # # *** To enable multi-domain support execute: # - enable mysql # - define WITH_MULTIDOMAIN # # *** To enable TLS support execute: # - adjust CFGDIR/tls.cfg as needed # - define WITH_TLS # # *** To enable XMLRPC support execute: # - define WITH_XMLRPC # - adjust route[XMLRPC] for access policy # # *** To enable anti-flood detection execute: # - adjust pike and htable=>ipban settings as needed (default is # block if more than 16 requests in 2 seconds and ban for 300 seconds) # - define WITH_ANTIFLOOD # # *** To block 3XX redirect replies execute: # - define WITH_BLOCK3XX # # *** To enable VoiceMail routing execute: # - define WITH_VOICEMAIL # - set the value of voicemail.srv_ip # - adjust the value of voicemail.srv_port # # # *** To enable IPv6 routing execute: # - define WITH_IPV6 # - define ADDR_IPV4 to server's IPv4 address # - define ADDR_IPV6 to server's IPv6 address # - enable nat traversal # * run RTPProxy in bridge mode between ADDR_IPV4 and ADDR_IPV6 # * - RTPProxy options: -l ADDR_IPV4 -6 /ADDR_IPV6 # # *** To enhance accounting execute: # - enable mysql # - define WITH_ACCDB # - add following columns to database #!ifdef ACCDB_COMMENT ALTER TABLE acc ADD COLUMN src_user VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE acc ADD COLUMN src_domain VARCHAR(128) NOT NULL DEFAULT ''; ALTER TABLE acc ADD COLUMN dst_ouser VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE acc ADD COLUMN dst_user VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE acc ADD COLUMN dst_domain VARCHAR(128) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN src_user VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN src_domain VARCHAR(128) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN dst_ouser VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN dst_user VARCHAR(64) NOT NULL DEFAULT ''; ALTER TABLE missed_calls ADD COLUMN dst_domain VARCHAR(128) NOT NULL DEFAULT ''; #!endif ####### Defined Values ######### #!define WITH_MYSQL #!define WITH_AUTH #!define WITH_USRLOCDB #!define WITH_NAT #!define WITH_IPV6 #!define ADDR_IPV4 192.168.178.26 #!define ADDR_IPV6 [fec0:0:0:1001::1] # *** Value defines - IDs used later in config #!ifdef WITH_MYSQL # - database URL - used to connect to database server by modules such # as: auth_db, acc, usrloc, a.s.o. #!define DBURL "mysql://openser:openserrw@localhost/openser" #!endif #!ifdef WITH_MULTIDOMAIN # - the value for 'use_domain' parameters #!define MULTIDOMAIN 1 #!else #!define MULTIDOMAIN 0 #!endif # - flags # FLT_ - per transaction (message) flags # FLB_ - per branch flags #!define FLT_ACC 1 #!define FLT_ACCMISSED 2 #!define FLT_ACCFAILED 3 #!define FLT_NATS 5 #!define FLB_NATB 1 #!define FLB_NATSIPPING 2 #!define FLB_IPV6 6 #!define FLB_V4V6 7 ####### Global Parameters ######### #!ifdef WITH_DEBUG debug=4 log_stderror=yes #!else debug=2 log_stderror=no #!endif memdbg=5 memlog=5 log_facility=LOG_LOCAL0 fork=yes children=4 /* uncomment the next line to disable TCP (default on) */ #disable_tcp=yes /* uncomment the next line to disable the auto discovery of local aliases based on reverse DNS on IPs (default on) */ #auto_aliases=no /* add local domain aliases */ #alias="sip.mydomain.com" #!ifdef WITH_IPV6 listen=ADDR_IPV4 listen=ADDR_IPV6 #!else /* uncomment and configure the following line if you want Kamailio to bind on a specific interface/port/proto (default bind on all available) */ #listen=udp:10.0.0.10:5060 #!endif /* port to listen to * - can be specified more than once if needed to listen on many ports */ port=5060 #!ifdef WITH_TLS enable_tls=yes #!endif ####### Custom Parameters ######### # These parameters can be modified runtime via RPC interface # - see the documentation of 'cfg_rpc' module. # # Format: group.id = value 'desc' description # Access: $sel(cfg_get.group.id) or @cfg_get.group.id # #!ifdef WITH_PSTN # PSTN GW Routing # # - pstn.gw_ip: valid IP or hostname as string value, example: # pstn.gw_ip = "10.0.0.101" desc "My PSTN GW Address" # # - by default is empty to avoid misrouting pstn.gw_ip = "" desc "PSTN GW Address" #!endif #!ifdef WITH_VOICEMAIL # VoiceMail Routing on offline, busy or no answer # # - by default Voicemail server IP is empty to avoid misrouting voicemail.srv_ip = "" desc "VoiceMail IP Address" voicemail.srv_port = "5060" desc "VoiceMail Port" #!endif ####### Modules Section ######## # set paths to location of modules #!ifdef LOCAL_TEST_RUN mpath="modules_k:modules" #!else mpath="/usr/local/lib/kamailio/modules_k/:/usr/local/lib/kamailio/modules/" #!endif #!ifdef WITH_MYSQL loadmodule "db_mysql.so" #!endif loadmodule "mi_fifo.so" loadmodule "kex.so" loadmodule "tm.so" loadmodule "tmx.so" loadmodule "sl.so" loadmodule "rr.so" loadmodule "pv.so" loadmodule "maxfwd.so" loadmodule "usrloc.so" loadmodule "registrar.so" loadmodule "textops.so" loadmodule "siputils.so" loadmodule "xlog.so" loadmodule "sanity.so" loadmodule "ctl.so" loadmodule "mi_rpc.so" loadmodule "acc.so" #!ifdef WITH_AUTH loadmodule "auth.so" loadmodule "auth_db.so" #!ifdef WITH_IPAUTH loadmodule "permissions.so" #!endif #!endif #!ifdef WITH_ALIASDB loadmodule "alias_db.so" #!endif #!ifdef WITH_SPEEDDIAL loadmodule "speeddial.so" #!endif #!ifdef WITH_MULTIDOMAIN loadmodule "domain.so" #!endif #!ifdef WITH_PRESENCE loadmodule "presence.so" loadmodule "presence_xml.so" #!endif #!ifdef WITH_NAT loadmodule "nathelper.so" loadmodule "rtpproxy.so" #!endif #!ifdef WITH_TLS loadmodule "tls.so" #!endif #!ifdef WITH_ANTIFLOOD loadmodule "htable.so" loadmodule "pike.so" #!endif #!ifdef WITH_XMLRPC loadmodule "xmlrpc.so" #!endif #!ifdef WITH_DEBUG loadmodule "debugger.so" #!endif # ----------------- setting module-specific parameters --------------- # ----- mi_fifo params ----- modparam("mi_fifo", "fifo_name", "/tmp/kamailio_fifo") # ----- tm params ----- # auto-discard branches from previous serial forking leg modparam("tm", "failure_reply_mode", 3) # default retransmission timeout: 30sec modparam("tm", "fr_timer", 30000) # default invite retransmission timeout after 1xx: 120sec modparam("tm", "fr_inv_timer", 120000) # ----- rr params ----- # add value to ;lr param to cope with most of the UAs modparam("rr", "enable_full_lr", 1) # do not append from tag to the RR (no need for this script) modparam("rr", "append_fromtag", 0) # ----- registrar params ----- modparam("registrar", "method_filtering", 1) /* uncomment the next line to disable parallel forking via location */ # modparam("registrar", "append_branches", 0) /* uncomment the next line not to allow more than 10 contacts per AOR */ #modparam("registrar", "max_contacts", 10) # ----- acc params ----- /* what special events should be accounted ? */ modparam("acc", "early_media", 0) modparam("acc", "report_ack", 0) modparam("acc", "report_cancels", 0) /* by default ww do not adjust the direct of the sequential requests. if you enable this parameter, be sure the enable "append_fromtag" in "rr" module */ modparam("acc", "detect_direction", 0) /* account triggers (flags) */ modparam("acc", "log_flag", FLT_ACC) modparam("acc", "log_missed_flag", FLT_ACCMISSED) modparam("acc", "log_extra", "src_user=$fU;src_domain=$fd;dst_ouser=$tU;dst_user=$rU;dst_domain=$rd") modparam("acc", "failed_transaction_flag", FLT_ACCFAILED) /* enhanced DB accounting */ #!ifdef WITH_ACCDB modparam("acc", "db_flag", FLT_ACC) modparam("acc", "db_missed_flag", FLT_ACCMISSED) modparam("acc", "db_url", DBURL) modparam("acc", "db_extra", "src_user=$fU;src_domain=$fd;dst_ouser=$tU;dst_user=$rU;dst_domain=$rd") #!endif # ----- usrloc params ----- /* enable DB persistency for location entries */ #!ifdef WITH_USRLOCDB modparam("usrloc", "db_url", DBURL) modparam("usrloc", "db_mode", 2) modparam("usrloc", "use_domain", MULTIDOMAIN) #!endif # ----- auth_db params ----- #!ifdef WITH_AUTH modparam("auth_db", "db_url", DBURL) modparam("auth_db", "calculate_ha1", yes) modparam("auth_db", "password_column", "password") modparam("auth_db", "load_credentials", "") modparam("auth_db", "use_domain", MULTIDOMAIN) # ----- permissions params ----- #!ifdef WITH_IPAUTH modparam("permissions", "db_url", DBURL) modparam("permissions", "db_mode", 1) #!endif #!endif # ----- alias_db params ----- #!ifdef WITH_ALIASDB modparam("alias_db", "db_url", DBURL) modparam("alias_db", "use_domain", MULTIDOMAIN) #!endif # ----- speedial params ----- #!ifdef WITH_SPEEDDIAL modparam("speeddial", "db_url", DBURL) modparam("speeddial", "use_domain", MULTIDOMAIN) #!endif # ----- domain params ----- #!ifdef WITH_MULTIDOMAIN modparam("domain", "db_url", DBURL) # use caching modparam("domain", "db_mode", 1) # register callback to match myself condition with domains list modparam("domain", "register_myself", 1) #!endif #!ifdef WITH_PRESENCE # ----- presence params ----- modparam("presence", "db_url", DBURL) # ----- presence_xml params ----- modparam("presence_xml", "db_url", DBURL) modparam("presence_xml", "force_active", 1) #!endif #!ifdef WITH_NAT # ----- rtpproxy params ----- # modparam("rtpproxy", "rtpproxy_sock", "udp:127.0.0.1:7722") modparam("rtpproxy", "rtpproxy_sock", "unix:/var/run/rtpproxy/rtpproxy.sock") # ----- nathelper params ----- modparam("nathelper", "natping_interval", 30) modparam("nathelper", "ping_nated_only", 1) modparam("nathelper", "sipping_bflag", FLB_NATSIPPING) modparam("nathelper", "sipping_from", "sip:pinger@kamailio.org") # params needed for NAT traversal in other modules modparam("nathelper|registrar", "received_avp", "$avp(RECEIVED)") modparam("usrloc", "nat_bflag", FLB_NATB) #!endif #!ifdef WITH_TLS # ----- tls params ----- modparam("tls", "config", "/usr/local/etc/kamailio/tls.cfg") #!endif #!ifdef WITH_ANTIFLOOD # ----- pike params ----- modparam("pike", "sampling_time_unit", 2) modparam("pike", "reqs_density_per_unit", 16) modparam("pike", "remove_latency", 4) # ----- htable params ----- # ip ban htable with autoexpire after 5 minutes modparam("htable", "htable", "ipban=>size=8;autoexpire=300;") #!endif #!ifdef WITH_XMLRPC # ----- xmlrpc params ----- modparam("xmlrpc", "route", "XMLRPC"); modparam("xmlrpc", "url_match", "^/RPC") #!endif #!ifdef WITH_DEBUG # ----- debugger params ----- modparam("debugger", "cfgtrace", 1) #!endif ####### Routing Logic ######## # Main SIP request routing logic # - processing of any incoming SIP request starts with this route route { # per request initial checks route(REQINIT); # NAT detection route(NATDETECT); # handle requests within SIP dialogs route(WITHINDLG); ### only initial requests (no To tag) # CANCEL processing if (is_method("CANCEL")) { if (t_check_trans()) t_relay(); exit; } t_check_trans(); # authentication route(AUTH); # record routing for dialog forming requests (in case they are routed) # - remove preloaded route headers remove_hf("Route"); if (is_method("INVITE|SUBSCRIBE")) record_route(); # account only INVITEs if (is_method("INVITE")) { setflag(FLT_ACC); # do accounting } # dispatch requests to foreign domains route(SIPOUT); ### requests for my local domains # handle presence related requests route(PRESENCE); # handle registrations route(REGISTRAR); if ($rU==$null) { # request with no Username in RURI sl_send_reply("484","Address Incomplete"); exit; } # dispatch destinations to PSTN route(PSTN); # user location service route(LOCATION); route(RELAY); } route[RELAY] { # enable additional event routes for forwarded requests # - serial forking, RTP relaying handling, a.s.o. if (is_method("INVITE|SUBSCRIBE")) { t_on_branch("MANAGE_BRANCH"); t_on_reply("MANAGE_REPLY"); } if (is_method("INVITE")) { t_on_failure("MANAGE_FAILURE"); } if (!t_relay()) { sl_reply_error(); } exit; } # Per SIP request initial checks route[REQINIT] { #!ifdef WITH_ANTIFLOOD # flood dection from same IP and traffic ban for a while # be sure you exclude checking trusted peers, such as pstn gateways # - local host excluded (e.g., loop to self) if(src_ip!=myself) { if($sht(ipban=>$si)!=$null) { # ip is already blocked xdbg("request from blocked IP - $rm from $fu (IP:$si:$sp)\n"); exit; } if (!pike_check_req()) { xlog("L_ALERT","ALERT: pike blocking $rm from $fu (IP:$si:$sp)\n"); $sht(ipban=>$si) = 1; exit; } } #!endif if (!mf_process_maxfwd_header("10")) { sl_send_reply("483","Too Many Hops"); exit; } if(!sanity_check("1511", "7")) { xlog("Malformed SIP message from $si:$sp\n"); exit; } } # Handle requests within SIP dialogs route[WITHINDLG] { if (has_totag()) { # sequential request withing a dialog should # take the path determined by record-routing if (loose_route()) { if (is_method("BYE")) { setflag(FLT_ACC); # do accounting ... setflag(FLT_ACCFAILED); # ... even if the transaction fails } if ( is_method("ACK") ) { # ACK is forwarded statelessy route(NATMANAGE); } route(RELAY); } else { if (is_method("SUBSCRIBE") && uri == myself) { # in-dialog subscribe requests route(PRESENCE); exit; } if ( is_method("ACK") ) { if ( t_check_trans() ) { # no loose-route, but stateful ACK; # must be an ACK after a 487 # or e.g. 404 from upstream server t_relay(); exit; } else { # ACK without matching transaction ... ignore and discard exit; } } sl_send_reply("404","Not here"); } exit; } } # Handle SIP registrations route[REGISTRAR] { if (is_method("REGISTER")) { if(isflagset(FLT_NATS)) { setbflag(FLB_NATB); # uncomment next line to do SIP NAT pinging ## setbflag(FLB_NATSIPPING); } if(af==INET6) setbflag(FLB_IPV6); if (!save("location")) sl_reply_error(); exit; } } # USER location service route[LOCATION] { #!ifdef WITH_SPEEDIAL # search for short dialing - 2-digit extension if($rU=~"^[0-9][0-9]$") sd_lookup("speed_dial"); #!endif #!ifdef WITH_ALIASDB # search in DB-based aliases alias_db_lookup("dbaliases"); #!endif $avp(oexten) = $rU; if (!lookup("location")) { $var(rc) = $rc; route(TOVOICEMAIL); t_newtran(); switch ($var(rc)) { case -1: case -3: send_reply("404", "Not Found"); exit; case -2: send_reply("405", "Method Not Allowed"); exit; } } # when routing via usrloc, log the missed calls also if (is_method("INVITE")) { setflag(FLT_ACCMISSED); } } # Presence server route route[PRESENCE] { if(!is_method("PUBLISH|SUBSCRIBE")) return; #!ifdef WITH_PRESENCE if (!t_newtran()) { sl_reply_error(); exit; }; if(is_method("PUBLISH")) { handle_publish(); t_release(); } else if( is_method("SUBSCRIBE")) { handle_subscribe(); t_release(); } exit; #!endif # if presence enabled, this part will not be executed if (is_method("PUBLISH") || $rU==$null) { sl_send_reply("404", "Not here"); exit; } return; } # Authentication route route[AUTH] { #!ifdef WITH_AUTH if (is_method("REGISTER")) { # authenticate the REGISTER requests (uncomment to enable auth) if (!www_authorize("$td", "subscriber")) { www_challenge("$td", "0"); exit; } if ($au!=$tU) { sl_send_reply("403","Forbidden auth ID"); exit; } } else { #!ifdef WITH_IPAUTH if(allow_source_address()) { # source IP allowed return; } #!endif # authenticate if from local subscriber if (from_uri==myself) { if (!proxy_authorize("$fd", "subscriber")) { proxy_challenge("$fd", "0"); exit; } if (is_method("PUBLISH")) { if ($au!=$fU || $au!=$tU) { sl_send_reply("403","Forbidden auth ID"); exit; } if ($au!=$rU) { sl_send_reply("403","Forbidden R-URI"); exit; } #!ifdef WITH_MULTIDOMAIN if ($fd!=$rd) { sl_send_reply("403","Forbidden R-URI domain"); exit; } #!endif } else { if ($au!=$fU) { sl_send_reply("403","Forbidden auth ID"); exit; } } consume_credentials(); # caller authenticated } else { # caller is not local subscriber, then check if it calls # a local destination, otherwise deny, not an open relay here if (!uri==myself) { sl_send_reply("403","Not relaying"); exit; } } } #!endif return; } # Caller NAT detection route route[NATDETECT] { if(af==INET6) return; #!ifdef WITH_NAT force_rport(); if (nat_uac_test("19")) { if (is_method("REGISTER")) { fix_nated_register(); } else { fix_nated_contact(); } setflag(FLT_NATS); } #!endif return; } # RTPProxy control route[NATMANAGE] { #!ifdef WITH_NAT if (is_request()) { if(has_totag()) { if(check_route_param("nat=yes")) { setbflag(FLB_NATB); } else { if(check_route_param("nat=v46")) { setbflag(FLB_V4V6); } } } } if (!(isflagset(FLT_NATS) || isbflagset(FLB_NATB) || isbflagset(FLB_V4V6))) return; if(isbflagset(FLB_V4V6)) { if(af==INET6) { rtpproxy_manage("FAEI"); } else { rtpproxy_manage("FAIE"); } } else { if(af==INET6) { rtpproxy_manage("FAEE"); } else { rtpproxy_manage("FAII"); } } if (is_request()) { if (!has_totag()) { if(isbflagset(FLB_V4V6)) { add_rr_param(";nat=v46"); } else { add_rr_param(";nat=yes"); } } } if (is_reply()) { if(isbflagset(FLB_NATB)) { if(af==INET) { fix_nated_contact(); } } } #!endif return; } # Routing to foreign domains route[SIPOUT] { if (!uri==myself) { append_hf("P-hint: outbound\r\n"); route(RELAY); } } # PSTN GW routing route[PSTN] { #!ifdef WITH_PSTN # check if PSTN GW IP is defined if (strempty($sel(cfg_get.pstn.gw_ip))) { xlog("SCRIPT: PSTN rotuing enabled but pstn.gw_ip not defined\n"); return; } # route to PSTN dialed numbers starting with '+' or '00' # (international format) # - update the condition to match your dialing rules for PSTN routing if(!($rU=~"^(\+|00)[1-9][0-9]{3,20}$")) return; # only local users allowed to call if(from_uri!=myself) { sl_send_reply("403", "Not Allowed"); exit; } $ru = "sip:" + $rU + "@" + $sel(cfg_get.pstn.gw_ip); route(RELAY); exit; #!endif return; } # XMLRPC routing #!ifdef WITH_XMLRPC route[XMLRPC] { # allow XMLRPC from localhost if ((method=="POST" || method=="GET") && (src_ip==127.0.0.1)) { # close connection only for xmlrpclib user agents (there is a bug in # xmlrpclib: it waits for EOF before interpreting the response). if ($hdr(User-Agent) =~ "xmlrpclib") set_reply_close(); set_reply_no_connect(); dispatch_rpc(); exit; } send_reply("403", "Forbidden"); exit; } #!endif # route to voicemail server route[TOVOICEMAIL] { #!ifdef WITH_VOICEMAIL if(!is_method("INVITE")) return; # check if VoiceMail server IP is defined if (strempty($sel(cfg_get.voicemail.srv_ip))) { xlog("SCRIPT: VoiceMail rotuing enabled but IP not defined\n"); return; } if($avp(oexten)==$null) return; $ru = "sip:" + $avp(oexten) + "@" + $sel(cfg_get.voicemail.srv_ip) + $sel(cfg_get.voicemail.srv_port); route(RELAY); exit; #!endif return; } # detect if IPv4 - IPv6 bridging is needed route[IPV4V6] { if(!has_totag()) { if(af==INET6 && !isbflagset(FLB_IPV6)) { setbflag(FLB_V4V6); } else { if(af==INET && isbflagset(FLB_IPV6)) { setbflag(FLB_V4V6); } } return; } } # manage outgoing branches branch_route[MANAGE_BRANCH] { xdbg("new branch [$T_branch_idx] to $ru\n"); route(IPV4V6); route(NATMANAGE); } # manage incoming replies onreply_route[MANAGE_REPLY] { xdbg("incoming reply\n"); if(status=~"[12][0-9][0-9]") route(NATMANAGE); } # manage failure routing cases failure_route[MANAGE_FAILURE] { route(NATMANAGE); if (t_is_canceled()) { exit; } #!ifdef WITH_BLOCK3XX # block call redirect based on 3xx replies. if (t_check_status("3[0-9][0-9]")) { t_reply("404","Not found"); exit; } #!endif #!ifdef WITH_VOICEMAIL # serial forking # - route to voicemail on busy or no answer (timeout) if (t_check_status("486|408")) { route(TOVOICEMAIL); exit; } #!endif }
Remarks
With this kind of deployment, you can have SIP/VoIP conversations like:
- IPv4 to IPv4
- IPv6 to IPv6
- IPv4 to IPv6
- IPv6 to IPv4
The communication is not limited to voice and video, you can do Instant Messaging, Presence notifications of Desktop sharing as well.
The NAT concept is gone in IPv6, however the platform is intended to run in mixed environment, therefore you can still see NAT traversal handling logic, being just ignored in IPv6.